
What Is Phishing?
Thursday 20 October, 2022

Phishing is the fraudulent practice of manipulating people via emails, texts, websites or phone calls into disclosing sensitive information, like credit card numbers or login credentials, that can then be used to access and attack systems. Cybercriminals do this by tricking users into taking specific actions that cause them to inadvertently download malware.
When successful, a phishing attack results in identity theft, data breaches, financial losses and other serious consequences for an individual or a business. It is one of the most common forms of social engineering — about 90% of data breaches begin with phishing. In recent years, phishing attacks have been increasing by 400% YoY.
Phishing is a hacking technique that exploits and manipulates human behavior for success. The attacker generally pretends to be someone the victim trusts, like a colleague or a bank representative, and creates a sense of urgency to rush the victim into making a rash decision and take a particular action. It's an effective hacking tactic because users can be gullible and forced to make mistakes. According to the World Economic Forum, 95% of cybersecurity incidents could be traced back to human error. Hackers find it easier to deceive people more than computers. Phishing is a profitable activity, with hackers earning about $4.91 million on average per attack.
Common types of phishing attacks
With hackers continuously evolving and innovating new forms of phishing attacks, here are some common of the more common ones seen in recent times.
Bulk phishing
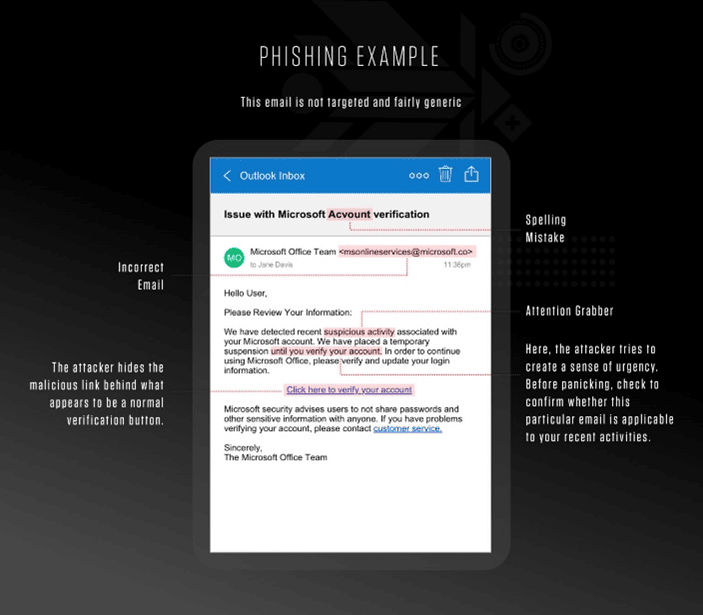
The attacker pretends to be a large, well-known organization like Netflix, Amazon or Microsoft to scam as many people as possible. They view this as a numbers game and tap into a common and strong emotion like fear or curiosity. Subject lines are usually something like “There is a problem with your order” or “Your documents are now ready.” The body contains the call to action, which seems logical and reasonable but is designed to trick the reader into visiting a hacked website or downloading an illegitimate file. They are also designed to look like legitimate messages, so users must know what to look out for to tell if a message is suspicious.

Spear phishing
In stark contrast to the last type we discussed, spear phishing is not for the masses. It's designed for specific targets — like someone with exclusive access to sensitive information or the power to authorize financial transactions. The attacker usually studies their victims by gathering as much information on them as possible — who they interact with and how, what's on their social media, etc. Similar to con artists, they use all this information to impersonate someone the victim knows — usually their boss or a colleague or vendor — and then try to lure the victim into making a mistake by presenting a credible request. The message could read something like “I know you're going on vacation. Could you clear this invoice before going?”
Spear phishing attacks are successful because the victim doesn't notice anything “phishy” about the request they receive. They then fall for it by making a payment or taking some other action that the attacker desires.
Whaling
This is basically like spear phishing but the victim is usually a senior executive or someone high up in the business hierarchy, so the attacker can make more money. The messaging and tactics followed by the attacker for all practical purposes is the same as in spear phishing.

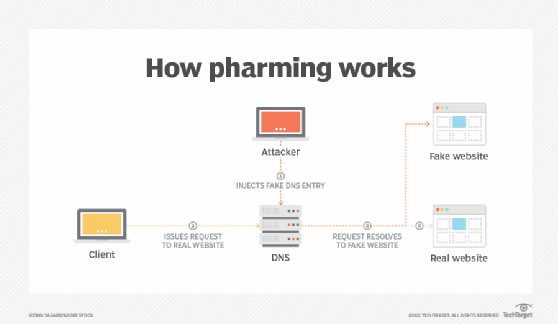
Pharming
Pharming is a sophisticated phishing attack that tricks the victim's DNS server (or device) into caching false information so that the victim is automatically redirected from a legitimate website to a fake one that's designed to capture their credentials.
Clone phishing
Clone phishing is a technique through which attackers use copies of legitimate emails or messages that the victim has already received before, and therefore, know and trust. The attacker will change some details and include malicious links or files in these copies. These suspicious changes are usually overlooked by the victim due to a sense of familiarity with the message.
How to avoid the bait — protecting against phishing
Despite the rise in phishing threats, 97% of employees don't know how to recognize an advanced phishing email. Education through security awareness training and phishing simulation (deliberately sending fake phishing emails to increase awareness) is the best way to combat this growing menace. According to a Webroot survey, around 11% of users fell victim to the first phishing email. However, this rate dropped significantly to 6% after the sixth simulation email and only 4% after 18 simulations.
Training helps users understand what phishing is and helps them identify what's “phishy” about the emails and messages they receive. “Phishy” traits include (but are not restricted to):
- Call to disclose sensitive or personal information or take any other action
- Requests for money
- Unsolicited files and attachments
- Subtle or blatant attempts to create urgency
- Threats of serious repercussions, sometimes unrealistic
- Poor spelling and grammar
- Illegitimate or incorrect sender details
- Truncated links that are hard to verify
- Links with subtle spelling differences that look genuine but aren't
- Malicious links that are misrepresented to look like genuine ones
Use technologies that help protect against phishing and its aftermath
- Advanced email security: It leverages machine learning and artificial intelligence to help users stay ahead of the latest phishing scams.
- Antivirus software: Phishing attacks bypass traditional security software because they don't contain malware. Advanced antivirus protection can provide an additional layer of protection if a successful attack has resulted in malware being deployed.
- Multifactor authentication (MFA): Phishing attacks typically harvest user credentials like username and passwords. MFA uses an extra mechanism to authenticate the user (e.g., via the mobile phone) and adds an extra layer of security so that even if the criminal has the password, it is useless because they cannot complete the MFA process.
- Web filters: These prevent users from visiting malicious and blacklisted websites.
What is phishing and how to combat it
Phishing is the fraudulent practice of sending fake emails and other messages to collect sensitive information or manipulate someone. It's a common menace and can be seen in many forms like spear phishing, whaling and pharming. The best way to protect against phishing is by educating users and adopting technologies that combat phishing, like email security solutions, antivirus software, etc.
We hope this blog shed some light on what phishing is and helped you understand how you can protect yourself and others against it.
Share on
More Blog Stories
Check out our recent stories from our blog that our editors selected for you




